You might have played some stunts on a linux, unix environment or even some sites and got this fired up to your face:
—–END PGP PUBLIC KEY BLOCK—–
Lovely I guess. But let’s really figure out what exactly it is.
You will have to blame Phil Zimmermann (the developer of PGP in 1991) for all this nonsense that can really be of great help to you.
What’s up with the PGP?
Pretty Good Privacy (PGP) is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting and decrypting texts, E-mails, files, directories and whole disk partitions to increase the security of e-mail communications.
Before even going further, we need to check what’s the whole thing about.
Cryptography
According to one Binarylife:
Cryptography is the science of using mathematics to encrypt and decrypt data. Cryptography enables you to store sensitive information or transmit it across insecure networks (like the Internet) so that it cannot be read by anyone except the intended recipient. While cryptography is the science of securing data, cryptanalysis is the science of analyzing and breaking secure communication. Classical cryptanalysis involves an interesting combination of analytical reasoning, application of mathematical tools, pattern finding, patience, determination, and luck. Cryptanalyst’s are also called attackers.
How does cryptography work?
A cryptographic algorithm, or cipher, is a mathematical function used in the encryption and decryption process. A cryptographic algorithm works in combination with a key � a word, number, or phrase � to encrypt the plaintext. The same plaintext encrypts to different ciphertext with different keys. The security of encrypted data is entirely dependent on two things: the strength of the cryptographic algorithm and the secrecy of the key. A cryptographic algorithm, plus all possible keys and all the protocols that make it work comprise a cryptosystem. PGP is a cryptosystem.
Public key cryptography is an asymmetric scheme that uses a pair of keys for encryption: a public key, which encrypts data, and a corresponding private, or secret key for decryption. You publish your public key to the world while keeping your private key secret. Anyone with a copy of your public key can then encrypt information that only you can read. Even people you have never met.
It is computationally infeasible to deduce the private key from the public key. Anyone who has a public key can encrypt information but cannot decrypt it. Only the person who has the corresponding private key can decrypt the information.
How does PGP work?
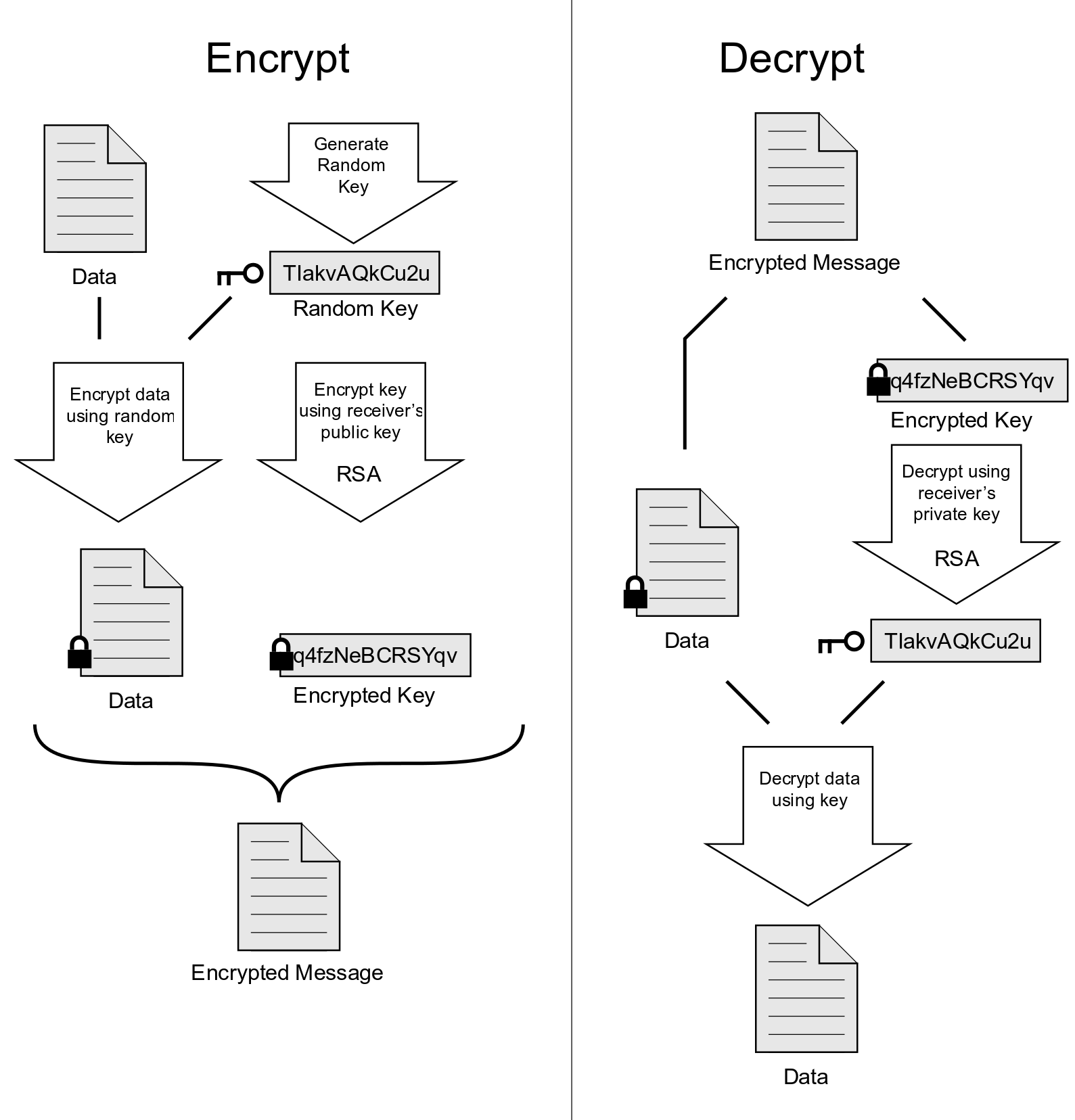
PGP combines some of the best features of both conventional and public key cryptography. PGP is a hybrid cryptosystem. When a user encrypts plaintext with PGP, PGP first compresses the plaintext. Data compression saves modem transmission time and disk space and, more importantly, strengthens cryptographic security. Most cryptanalysis techniques exploit patterns found in the plaintext to crack the cipher. Compression reduces these patterns in the plaintext, thereby greatly enhancing resistance to cryptanalysis. (Files that are too short to compress or which don’t compress well aren’t compressed.) PGP then creates a session key, which is a one-time-only secret key. This key is a random number generated from the random movements of your mouse and the keystrokes you type. This session key works with a very secure, fast conventional encryption algorithm to encrypt the plaintext; the result is ciphertext. Once the data is encrypted, the session key is then encrypted to the recipient’s public key. This public key-encrypted session key is transmitted along with the ciphertext to the recipient.
IS PGP REALLY SECURE?
Yes and no. Yes, it is secure against most attackers when used on a physically secure system in accordance with its instructions. This includes using a good passphrase to protect your private keys and keeping your passphrase and private keys truly private. You must also never run or allow to be run any rogue software (including viruses, worms, and Trojan horses) that might send your passphrase keystrokes and your PGP key file back to some spy.
If an adversary of yours has physical access to the computer that you use with PGP, it is not hard to install a hardware or software keystroke logger that can capture your passphrase, and to copy your private keyring. With that combination, any of your PGP-encrypted messages can be read. PGP is not secure if you don’t understand what you are doing. It is al
I stumbled on this Q&A session from PGP
Q: What is PGP?
A: PGP is a program that gives your electronic mail something that it otherwise doesn’t have: Privacy. It does this by encrypting your mail so that nobody but the intended person can read it. When encrypted, the message looks like a meaningless jumble of random characters. PGP has proven itself quite capable of resisting even the most sophisticated forms of analysis aimed at reading the encrypted text.
PGP can also be used to apply a digital signature to a message without encrypting it. This is normally used in public postings where you don’t want to hide what you are saying, but rather want to allow others to verify that the message actually came from you. Once a digital signature is created, it is impossible for anyone to modify either the message or the signature without the modification being detected by PGP.
While PGP seems (and according to many of its users is) easy to use, it does give you enough rope so that you can hang yourself. You should become thoroughly familiar with the various options in PGP before using it to send serious messages. For example, giving the command pgp -sat <filename> will only sign and ASCII armor a message, it will not encrypt it. Even though the output looks like it is encrypted, it really isn’t (it is the ASCII armor that looks so though). Anybody in the world would be able to recover the original text with a simple pgp <encryptedfilename>.
The graphical userinterface of PGP 5.x and higher also has its pittfalls, as Alma Whitten describes in Why Johnny Can’t Encrypt – A Usability Evaluation of PGP 5.0: even with manuals and an introduction, three of the twelve participants accidently sent “secret” information unencrypted.
WarningMake sure you thoroughly understand how to operate PGP prior to using it for confidential information.
A: You should encrypt your e-mail for the same reason that you don’t write all of your correspondence on the back of a post card. E-mail is actually far less secure than the postal system. With the post office, your mail is handled by postal workers. Take a look at the header area of any e-mail message that you receive and you will see that it has passed through a number of nodes on its way to you. Every one of these nodes presents the opportunity for snooping, as do all systems that can listen in on the communication between these nodes. Encryption in no way implies illegal activity. It is simply intended to keep personal thoughts personal.
Xenon puts it like this:
Crime? If you are not a politician, research scientist, investor, CEO, lawyer, celebrity, libertarian in a repressive society, investor, or person having too much fun, and you do not send e-mail about your private sex life, financial/political/legal/scientific plans, or gossip then maybe you don’t need PGP, but at least realize that privacy has nothing to do with crime and is in fact what keeps the world from falling apart. Besides, PGP is FUN. You never had a secret decoder ring? Boo!
Before you jump into thinking of using PGP or not, Check with the laws in your own country before using PGP or any other encryption product.
Go know yourself out if you wanna try this out!